
Atomic I/O letters column #160
Originally published 2014, in PC & Tech Authority(in which Atomic magazine is now a section)
Reprinted here February 22, 2015 Last modified 09-Apr-2015.
Where the magic happens
I have a nifty round orange "Powertech" four-outlet power board, which got left out in the rain after a party where I had my computer on the veranda for music. I thought I could probably rescue it and unscrewed the top and cleaned it all out, and it looks good as new now, but I'm curious: what are the three round blue things in there (see photo)?
This is supposed to be a surge protector, but those are the only components I can see in there besides copper wires, copper strips, a switch, what I take to be a circuit-breaker, and one little light.
How much protecting from surges do those round blue things actually do? Are they smoothing capacitors, which you've written about before? Should I be powering my computer from something better than this?
Ed
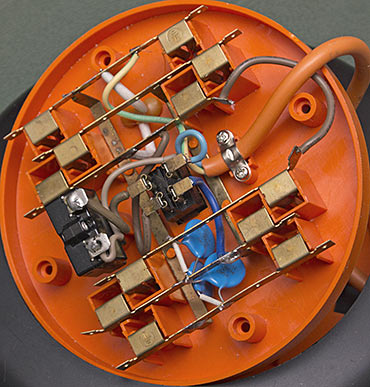
The guts of any normal powerboard, rolled up!
Answer:
The blue things are metal oxide varistors,
or "MOVs", and they are indeed the only component in a standard "surge protector" powerboard
that actually does any surge protecting. (The circuit-breaker is only there to trip
if you grossly overload the powerboard, or there's a short circuit. If you'd plugged
the powerboard in when it was still full of low-conductivity rainwater, the circuit
breaker probably wouldn't even have noticed. If your house has a
safety
switch in the breaker
box, though, that would have tripped.)
The picture resolution's good enough that I could read "471KD14" on those MOVs; search for that and you'll get datasheets for these precise components. What the datasheets don't say, because electrical engineers are expected to know it already, is that MOVs wear out. They will indeed protect you from surges, to some extent, but only a few big surges or several little ones. And then they might as well not be there at all.
Most "surge protectors" are in service for many years, which means that almost all "surge protectors" in use in the world don't protect from surges at all any more.
On the plus side, three MOVs don't provide very good surge protection in the first place, so you haven't lost much! And the power supplies for most computer gear are quite tolerant of ugly incoming mains, so unless you live somewhere with particularly unreliable power, you needn't worry about getting a better power filter. It's still nice to run your computer from an uninterruptible power supply, though, because that'll let you ride out brief power cuts that might not have damaged the PC, but certainly would have instantly turned it off and thereby maybe damaged some data.
(I've written about this before, in more detail.)
Cure worse than the disease?
Good news! My computer did not catch fire!
But the cheap fan heater next to it did, and my workmate seized the opportunity to grab the dry powder extinguisher off the wall and blast the flaming plastic, and because the side of my PC case is off (a whole other story there we need not get into), now the computer is full of extinguisher powder.
How disastrous is this? From past letters it seems you're the guy to ask about weird substances in PCs. I've already taken the computer outside and shaken all the obvious powder out. There's plenty left in nooks and crannies, though.
B.
Answer:
The powder in standard "dry
chemical" extinguishers is
bicarbonate of soda,
which is pretty kind to computer components. (If the powder is yellow then it's probably
monoammonium phosphate,
which is worse. But white powder plus cheap extinguisher equals bicarb.)
Bicarb dissolves readily in water to make a not-very-harmful alkaline solution (actually, it cuts grease and helps to clean many things), so you can clean it out of slots and out from under chips and so on with clean water. Remove moving-parts drives for separate cleaning, and then tapwater should be fine for the rest of the computer. Use demineralised water if you're fancy, but it really shouldn't make any difference.
(You can even get away with pouring a little water on hard drives, since none of it is likely to make it through the fibre-filtered breather hole. Don't come crying to me if you drown a drive, though.)
After washing, dry components very thoroughly with sun and breeze - especially if you're doing this the lazy way and cleaning things while they're still plugged together - and then the computer will have a surprisingly high probability of working fine. Pay attention to fans and heat sinks, though; fan bearings can get clogged with powder, and so can closely-spaced heat-sink fins.
If the weather doesn't cooperate, the new, less defective fan heater you will presumably soon be buying will also dry a computer effectively. Use low heat for more time than you'd think.
Stripes are slimming
My old Dell Inspiron 1545 suddenly has numerous randomly spaced green vertical stripes on the screen. Taking a screenshot and looking at it on another computer shows a normal picture, so I presume it's the screen that's the problem. Apart from that the laptop is fine, but it's not young and a new screen for it would probably cost more than a whole new laptop the same age. Is this worth fixing?
Alex
Answer:
The problem is almost certainly not the screen itself but the
ribbon cable or
flex circuit that goes
from the laptop mainboard to the screen, through the hinge of the laptop. That
ribbon cable gets bent every time you open and close the laptop, and cracked conductors
in the cable commonly result, after a while. (The only laptops immune to this problem
are the tablet-ish weirdoes that have the mainboard behind the screen, and little to
nothing below the keyboard. They only bend the simpler keyboard cable when opened and
closed.)
In your case, some wire responsible for the green subpixels (each LCD-screen pixel is made up of a red, a green and a blue subpixel) is locking them all on at some locations.
A normal human with an unremarkable set of screwdrivers can replace the screen ribbon cable in most laptops, and Dell have good downloadable PDF service manuals for their products. It's also not difficult to find a new or new-ish ribbon cable; I just did a quick eBay search and found several under $10 delivered.
If you've never done this before, just work slowly and think about what you're doing - so, for instance, don't yank cables out of their connectors without first checking for little plastic clips that hold them in. About the only way you can seriously screw up if you're slow and methodical is by doing electrostatic damage to components. To avoid that without needing a wrist-strap and conductive workmat and so on, just talismanically touch exposed metal on the laptop as you work, to keep your body and the laptop chassis at the same electrical potential.
Rotate tyre air, top up blinker fluid
When a computer shop (or big-brand chain...) offers a "tune up" or "optimisation" for extra money when you buy a new computer, what do they actually do?
I've asked, and got palaver about viruses (sell a lot of brand new computers with viruses already on them, do you lads?) and system performance (brand new computers with fragmented hard drives?). Is this literally money for nothing?
G.
Answer:
Not usually, but it can come pretty bleeding close.
One thing you can do to a new brand-name computer that genuinely will make it better is uninstall the shovelware it comes with - trial versions of crummy virus checkers, lousy Wi-Fi connection management hardware that does nothing the operating system itself can't already do, et cetera. The shovelware problem isn't as bad as it used to be (now crap like this usually arrives in the installer for some program you actually want...), but it's still out there. And it's still difficult to persuade, say, Sony, to not give you a bunch of Sony-branded folderol.
Apart from that, there should, as you say, not be anything on a new computer that needs tuning up. If the tune-up service does anything, it probably just prunes out some (allegedly...) unnecessary startup items, and/or charges you for the installation of free software, like Web browsers or one of the antivirus programs that're actually good.
Once you've been using a computer for a while and installed various things, pruning the startup items can make a significant difference. Msconfig.exe used to be the standard way of doing that; Autoruns is better. And if you want to look more competent than 90% of computer-shop "optimisers", try Ultimate Boot CD.
They've forgotten it too
Why, when you click the "forgot password" thing on a Web site, do they always give you a new password, not just tell you the old one? If they're worried about e-mail security which I suppose makes sense, how is it better to change a user's password, if that user wasn't the one who clicked "forgot password" in the first place?
Laurie
Answer:
They don't send you your password because they don't know what it is.
Standard procedure for computer password security is to run the password through a "hash function", which turns it into a string of random-looking characters, which are what the server stores. When someone tries to log in, the password they give is hashed the same way. If it matches the stored hash, they're allowed in.
(It's theoretically possible for two passwords to have the same hash, a so-called "hash collision". You are far more likely to be hit by a crashing jumbo jet while trying to log in to someone else's account than you are to come up with a hash-collision password that lets you in. It's possible to engineer hash collisions only if you have a vast number of possible hashes to "aim at".)
Password security works this way so that miscreants who get their hands on the username/password data cannot immediately use it to log in. Instead, they have to "reverse" the password hashes, which is computationally outrageously expensive.
Well, that's how it all used to work, at any rate. I last wrote about the state of play in password hackery only about seventy years ago, in computer time.
(Storing passwords as hashes also prevents the password-storage system from being
able to remember what you type, when you type in the wrong password. Being able
to remember that would be very helpful, for a criminal. This is because every day,
many people fail to log in to an online game or Web forum or whatever because they
accidentally typed the password for some other, perhaps much more important,
service. I, for instance, have absent-mindedly typed my
memorable-but-silly PayPal password into
MechWarrior Online several times, instead of the quite different but
similarly silly password that I set up for MWO.
Since MWO uses your e-mail address as your login user-name, if they were
malicious, they could easily store all login attempts in plaintext. Because many
people use the same password on many sites, just knowing the correct e-mail
address and online-game password for a lot of people will get you into numerous
PayPal and other valuable accounts, but plaintext login-attempt storage would also
let you automatically detect every attempted login with a the failed password that
is very different from the correct one. That catches people like me, who use
different passwords everywhere but sometimes type in the wrong one for where they
currently are. Given this information, a miscreant could try logging in to PayPal
with all of these promisingly-different address/password pairs, some of which would
definitely be from people who'd made the same mistake as me.
Given that my PayPal account has not been mysteriously drained, except when I
willingly purchase things which no sane
person would, it appears that the MWO admins are honest, and are running a
proper hashed-password storage system. A password-hash system can of course still
tell if someone enters the wrong password, but if all it stores is the hashes, then
it has no idea what that wrong password was, and there's not even any way to tell
whether the wrong password is very different from the correct one, or whether the
user only mistyped one character.)

