Atomic I/O letters column #152
Originally published 2014, in PC & Tech Authority(in which Atomic magazine is now a section)
Reprinted here December 8, 2014 Last modified 17-Nov-2015.
I, also, like to live dangerously
Can you charge a lithium ion battery without a proper charger, by just connecting a power supply of appropriate voltage to the correct terminals with paper clips and alligator clip leads and other such things? I've seen something like this done with a bench power supply at uni, but I don't know how dangerous it is, or isn't.
Kel

Rare-earth magnets make it easy to connect a battery
to something you shouldn't connect a battery to!
Answer:
Yes, you can do this, and it can get you out of trouble if there's no other way to charge
your laptop or phone or whatever. But it can also get you into rather more trouble.
This is one of those situations where asking the question means you probably don't have
enough experience to try it unsupervised.
Some "smart" batteries have internal hardware that won't allow them to charge, or even discharge, unless the right things are connected to the extra terminals that many rechargeable lithium batteries have in addition to the simple positive and negative.
Presuming you can get past that, an adjustable bench power supply can easily be set to deliver a battery's charged voltage, and most bench supplies also have current limiting. Careful application of these two features will make it difficult to quickly explode a lithium battery.
An explosion is still eminently possible, though, because a bench supply has no idea when the charge should be stopped. The safest thing to do is to wind the current limiting way back, and set the voltage to something below the normal charged voltage of the battery, but above its current un-charged terminal voltage, so it's impossible to overcharge the battery at all. You'll never fully charge it, either, but this is good enough for throwing a 20% charge into your phone battery so you can make another couple of calls, or whatever. You can do this with lithium-ion and lithium-polymer batteries, and all other consumer rechargeable chemistries - nickel metal hydride, nickel cadmium, lead acid.
If you're using something other than a bench supply, you can still stay reasonably safe if the voltage of the power supply you choose is appropriate to the thing you're charging. You can, for instance, probably get a useful charge into a flat 12-volt car battery by hooking it up to the 12V output of a PC power supply.
What's highly inadvisable is quick-charge techniques where you deliberately connect a battery to a high-current-capacity source with a substantially higher voltage than the battery should have even when fully charged.
Example of this from the olden days: Connecting a 7.2-volt model-car battery pack to a 12-volt car battery to charge, with only a resistor in the "charge cord" standing between the user and a burnt-out car. Example of this from today: Connecting a single-cell 3.6-volt phone battery directly to 5-volt USB power.
Shorting things out is an ever-present danger when you're doing this sort of hackery, too. Some lithium batteries will get hazardously excited if shorted...
...but fortunately many have some kind of protection cutout mechanism that temporarily or permanently disconnects the output terminals if they're overloaded. Every proper bench power supply is short-circuit protected. Car batteries, not so much.
Once you've mastered the above inadvisable activities, you can move on to charging batteries from things that output far too many volts, until you load them up by connecting the battery, whereupon their terminal voltage drops. You can, for instance, power or charge various things that expect USB power by connecting them directly to a standard nine-volt battery. But don't come crying to me if you blow something up.
(I once charged a car battery through super-skinny light-duty hookup wire, because I had that, and a bench supply. I could have run the bench supply out by the car with an extension cord and connected it to the battery via short chunky cables for a nice fast charge, but instead I ran forty feet of hookup wire from the bench supply indoors and just turned up the voltage on the 0-30V PSU until it overcame the voltage drop of all that fishing-line-thin copper. Left it all night with the current set low, and the car started fine in the morning!)
These sorts of tricks should only be attempted if you're in a real survival situation. Because then, if the charge fails, you may at least have successfully started a campfire!
Enhance!
I'm using a, I believe you call it "yum cha", unknown-brand LCD TV as a monitor for my living-room computer. The TV has analogue component inputs and two digital inputs, one HDMI and one DVI, and it even came with an HDMI cable, so I plugged it into my PC with that and the picture was... terrible. Sort of skinny halos around everything, and weird colours, and a sort of blurring effect on moving things, right down to the mouse pointer.
My computer has a DVI output too so I got a DVI cable and tried that, and it looks fine now. Viewing angles still not so great, but it was really cheap so I'm not complaining.
I thought the video signal for DVI and HDMI was the same, though, except for DRM and the possibility of audio as well on HDMI. Why do they look so different?
C.
Answer:
Most modern flatscreen TVs have "image enhancement" functions which do, arguably, make
some TV and movies look better. Your haloing effect probably came from sharpening, for
instance, and colour strangeness could be the result of punched-up saturation and contrast,
that psychedelic super-saturated look that TV shops often use to catch customer attention.
The blurry weirdness could be
interpolation meant
to boost the apparent frame rate and reduce flicker.
These sorts of features are often turned on by default when a TV thinks it's displaying television or movies, which is what your TV presumes HDMI input to be. It presumes DVI input to be from a computer, and doesn't use any of the enhancements then.
If you've got a screen that looks better with analogue input ("VGA", or even component cables) than with HDMI, this is probably the reason. You can probably also turn all of the enhancements off for HDMI, but I wouldn't bet on that being possible on the cheapest and most cheerful of TVs.
Insert plug A into hole B with club-hammer C
The rear ports on the motherboard of my PC don't line up properly with the holes in the metal cover at the back of the case, I think because the case itself isn't quite square. I can just about jam the USB and audio plugs in, but the network and PS/2 keyboard sockets have required me to prune a little plastic off the plugs.
I notice that the metal cover is a separate piece, not part of the main chassis of the case. Can you just remove it and leave the ports "nude"? Or is that a bad idea because of shielding or earthing or something?
Aaron
Answer:
Yes, you can just pull the port plate off and discard it. (If you don't care whether
it survives, you could probably grab it with pliers and yank it straight out through
the hole it sits in, without even taking the side off the case. All usual disclaimers
about computer destruction occurring because of my idiotic advice
apply.)
The cover is there partly for airflow reasons and partly, as you say, for RF shielding, but just making a hole that size in the back of the case is very unlikely to cause interference problems for anything. Computers that exceed quite strict RF interference standards are in many countries illegal to sell, but even a completely nude PC built on a plastic frame isn't likely to cause interference beyond messing up AM radio reception within a couple of metres.
Note that misaligned components in a PC may indeed be that way because the case is just a bit wonky, as many cheap PC cases are. But it's also possible that there's some gross problem, like a motherboard in trace-snapping tension because its mounting standoffs are different lengths, or a lever gadget that's meant to hold large video cards in place but is instead pushing the card to one side, and trying to pry the video slot off the motherboard.
Fixing a problem like that should cause everything to line up nicely again without requiring you to discard any pieces of the case. It can also protect you from sudden damage to your bank account.
Wanted: Series Of Tubes
What's the easiest way to map a network drive over the Internet?
Home-workers in my small company need to be able to access stuff on what passes for a server here (it's still running Windows XP), and really just one simple shared folder would do it, with a bit of security but no need to go nuts, we're not a big target for industrial espionage or international spy agencies.
I've tried Remote Desktop and Google cloud storage, but the boss says and I agree that just mapping a damn drive will do just fine if we can find some easy way to do it. I do not, very not, very strongly not, want to have to teach my traveling co-workers how to open ports on a router.
Any clues?
Patrick
Answer:
Use Hamachi. It's specifically
made to allow you to create an ad-hoc
virtual private network
(VPN) without messing around with router config, and it works on WinXP, and it doesn't
even cost money unless you want more than five devices connected.
Hamachi isn't going to give you 99.9999% uptime, ping times across the network from here in Australia probably won't be great, and I wouldn't trust its security with my plans to destroy NATO with this weather machine I'm building. But it looks as if it'll do what you want.
You can even use Hamachi to access Windows shares from a Mac, with very little more aggravation than you'd suffer with a "normal" network.
"Click here to not refuse negative non-installation of Ultra Registry BonziBuddy!"
Suddenly I have "McAfee VirusScan" on my computer (Windows 7 x64). I did not install it. So what I'm thinking is that it's some kind of virus that's pretending to be a common antivirus program. It doesn't seem to be doing anything bad, though, and I can't find anything online about such a program, though there are lots of other "fake antivirus" malware things.
Am I being too paranoid?
Sean
Answer:
You probably did install it. You just didn't mean to.
You know those irritating programs with an installer that has five extra pages in it that say "Install SuperWhizBang Toolbar" and "Sign up for 1050 free MP3s from DodgyTunes.ua" and so on? Sun have been playing these "foistware" tricks with the standard Java installer for years. (This kind of unrelated-software-sneaked-into-something-else's-installer is less pejoratively known as "installware", and slightly more pejoratively known as "drive-bys" or "shovelware". "Shovelware" can also mean low-quality software of little interest, like the stuff on discount-store "9999 Games For $5.99!" disks. Installer foistware is also sometimes called "bloatware", because it adds size to the installer that has nothing to do with the software you actually mean to install.)
When you installed Java, it installed the McAfee antivirus thing; it possibly still does it now, depending on when you're reading this. You have to specifically tell the installer not to do this.
The Flash Player installer is one of those hybrid Web/local deals; your opportunity to accidentally install McAfee foistware is presented on this Web page.
If you're lucky, a sneaky installer like this will only change your default search engine or something. The next rung up the foistware nuisance ladder are nigh-useless toolbars. Next come real but unwanted apps, like the McAfee free gift you're so delighted to have received. Then there are semi-spyware things like the "Search Protect" program that recent uTorrent versions installed with no option not to.
Foistware is usually not malware, strictly speaking; what's being foisted on you is usually something that you could imagine some person actually wanting, unlike actual viruses and fake antivirus programs and so on. And yes, money from foistware does help support small software companies that know most users will never buy the commercial version of whatever it is they make.
Microsoft and Adobe do it too, though, and I think they could probably afford not to.
After this letter appeared in the magazine, I kept collecting foistware examples, which I present below.
It would appear that if you want a really high quality and quantity of scammy foistware, you should choose software which is associated with illegal activity. (I theorise that this is because people who make, for instance, BitTorrent clients, know that there's little chance that they'll be able to directly and honestly extract money from their userbase composed almost entirely of pirates.)
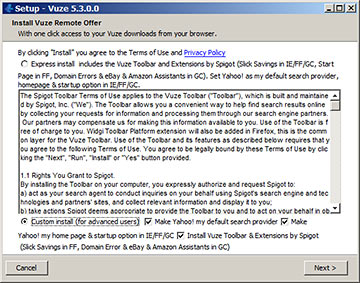
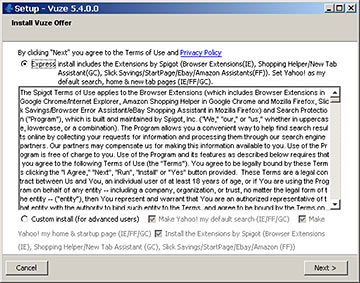
Take Vuze, for instance, the BitTorrent client formerly known as Azureus:
"Sure, why wouldn't I want some extra Vuze features- heyyyyy, waaaaaaiiiit a minute..."
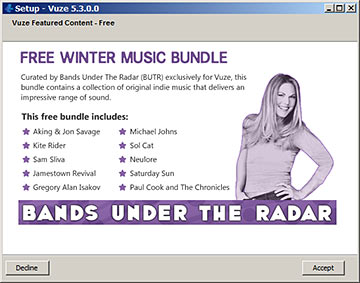
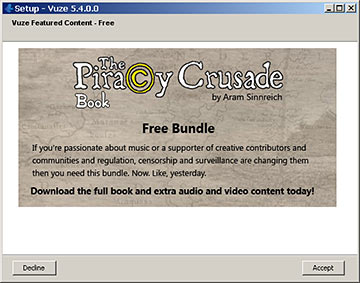
I think this was a perfectly kosher, legal bundle of free music. Any time I see a non-standard stage in an install process now, though, I presume it's trying to sneak some kind of crap onto my computer.
I wonder how many more listeners these up-and-coming bands would have had if their free music offer wasn't sandwiched between scams?
Hopping forward from the Vuze 5.3 installer to the 5.4 one... apparently all the good names were taken, so these guys were stuck with Spigot. They made the abovementioned "Search Protect", too.
Search Google for the name of this thing and, as I write this, all ten first-page results are removal instructions!
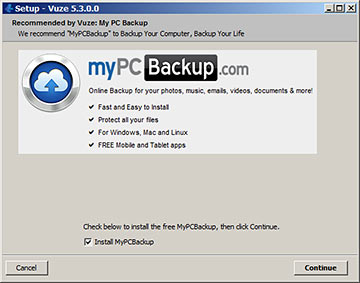
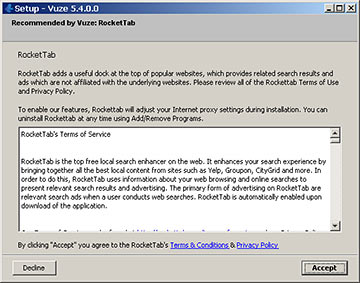
But now there was this, which I think is perfectly kosher, too.
Once again, though, it's a non-scam lost in a crowd of pickpockets and flim-flam men.
Another piece of software associated with illicit activity is the comic-book-archive viewer CDisplay Ex, which you can use to read un-pirated material but whose principal real-world purpose is to let people read comics they've downloaded illegally.
(The comic-book archive format is just a ZIP or RAR file full of sequentially named image files. Anyone can compile a comic-book archive from images of book pages, or any other images for that matter.)
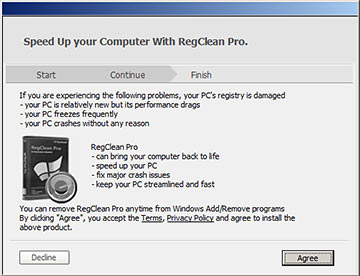
The previous version of CDisplay's installer presented me with a total of 13 different windows, most of which were the usual things saying where-do-you-want-it-installed, do-you-want-a-desktop-icon, and so on. But four of them gave these sterling shovelware opportunities:
I'm sure they mention the adware somewhere in that agreement.
Again, when most of the first page of Google hits for a program's name are pages on how to remove the damn thing, you might want to click that "Decline" button.
(You probably don't actually need a registry cleaner, but if you must have one, just get CCleaner, which has several other useful functions and will not suddenly demand you pay money to use them.)
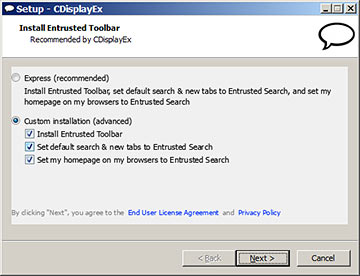
Well, this toolbar's "Entrusted", surely it can't be- Oh.
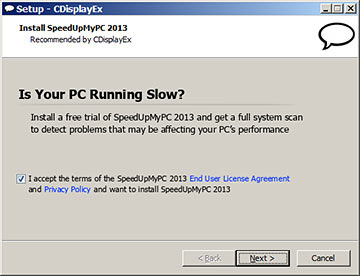
Why wouldn't you want to SpeedUpYourPC?! Uh, perhaps because, like most "PC cleaner" programs, it's actually mendacious "scareware".
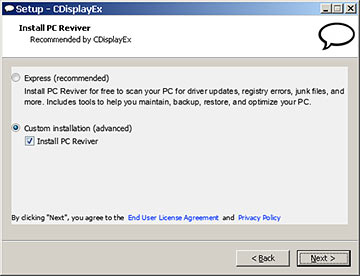
In the version of CDisplay that came out quite recently as I write this, there's yet another chance to install Search Protect, and you also get the frequently-to-be-repeated-offer of installing...
..."PC Reviver", with the novel non-installation system of selecting "Custom installation" and then unticking a box. After which, there's...
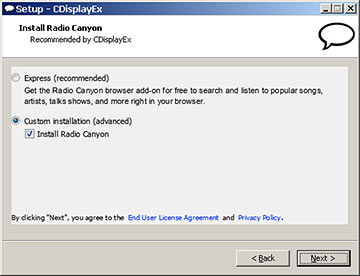
..."Radio Canyon", with the same half-hidden install-preventer.
I'm pretty sure you don't want Radio Canyon, but PC Reviver seems to not be malware. But that's damning it with extremely faint praise. All you're getting is the trial version of the commercial program, and PC Reviver doesn't seem to do anything that can't be done for free.
Daemon Tools is an immensely useful suite of disk-image utilities, but it's been touched by the magic wand of piracy too, because as well as using it to do perfectly legal things, people also use it to mount images of cracked game discs and copied video discs.
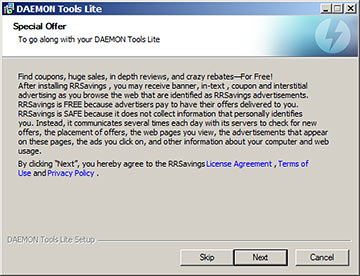
Perhaps that's why the Daemon Tools installer offers this:
"Crazy rebates", huh?
(This is another ten-out-of-ten removal-instructions Google-search winner. As I write this, one of the ten results in a search for "RRSavings" is from the makers, at rrsavings.com - but it's telling you how to turn the ads off, too!)
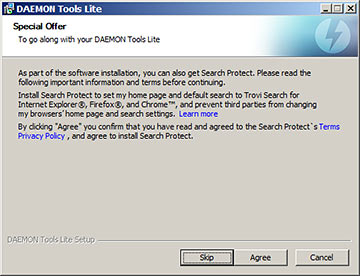
There's Search Protect from Spigot again. It guards against search- and homepage-hijacking malware... by changing those settings to use its own service!
(And then it starts popping up ads.)
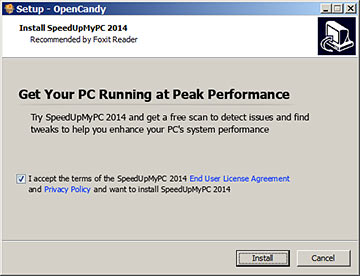
Here's SpeedUpMyPC again, this time trying to sneak in via the installer for Foxit Reader, a perfectly good PDF viewer.
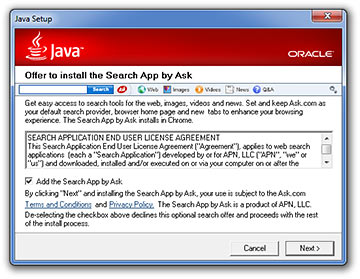
Are you tired of accurate, useful search results? Oh, boy, Oracle has got a deal for you!
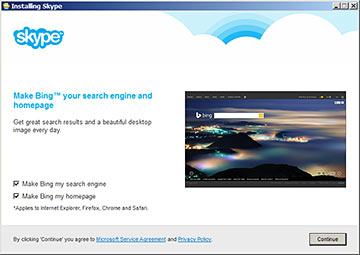
And finally, Microsoft owns Skype now, so it's hardly surprising that the Skype installer now tries to get you to use Bing. Which has its uses, but still ain't that great.
This Skype example is also the least evil form of foistware. All it does is change a couple of ordinary browser settings, which you can easily change back again later.