On the h4xx0ring of p4sswordZ
Publication date: 4 May 2013Originally published 2012 in Atomic: Maximum Power Computing
Last modified 04-May-2013.
Greetings, fellow criminals!
Today, I will be discussing recent happy developments in the profitable and entertaining field of stealing other people's Internet passwords.
This used to be quite annoying. Every now and then some idiot would leave ftp.someidiot.com/secret/passwords.txt just sitting there in plaintext, not the salted password hashes that they should have saved.
But usually it wasn't easy to get the hashed passwords, and then it was unacceptably computationally expensive for us to brute-force our way through passwords of ever-increasing length until we found some that matched the hashes. Brute-force cracking is getting faster and faster, but if the brute-forcing time for an 80486 was "one googolplex years", then even if modern hardware can do it a million times as fast, you're still not appreciably closer to the target.
Password hashes still aren't usually salted, of course, which is great. This is the sort of thing that gives computer criminals a reason to get up in the morning; it's one of the great scandals of computing, like how programs still have buffer-overflow vulnerabilities even though that was a solved problem when colour monitors were a luxury.
(Even today, practical IT security can involve the ignoble surrender of making buffer-overflow attacks more difficult, rather than fixing the code that makes them possible.)
If someone generates a pseudorandom several-character salt and adds it to the password before they hash it, there'll be no known hashes for us to use and instantly get the password.
There are also several well-known more-processor-intensive hashing systems. They don't put a significant extra load on a system that only has to deal with dozens, or even thousands, of new user accounts per hour, but they make brute-force guessing of passwords to match known hashed values take millions of times as long.
Fortunately, a ridiculous number of Web sites and other password systems stick with the old password-hash systems like SHA-1, which were a good idea when a 486 was a fast PC, but which are becoming less and less of a good idea now.
We, the computer criminals, can avoid the problems with brute-force attacks by doing dictionary attacks - trying words from a list, including both actual real "dictionary words" and common modifications and combinations of those words. That finds the people who thought "passw0rd1" or "jamesbond007" were good enough.
But many passwords are still too complicated for this to work, in which case we had to go back to pure brute-force. And if a password's reasonably long, brute-force remains too slow even when you're running at blinding speed against some file on your own system, let alone if you're trying to use a similar attack against some distant server.
Then affordable computers with gigabytes of RAM and fast CPUs came along, allowing the creation of "rainbow tables". A rainbow table provides the effect of reversing the hash of every possible password of a given length, without requiring impossible amounts of storage space. The storage requirements for rainbow tables were still impossible for a long time, but now that gigabytes of RAM and hundreds of gigabytes of disk space are cheap, the poorest among our criminal brethren can afford them.
You don't need rainbow tables for increasingly long passwords any more, though. Faster CPUs and reprogrammable graphics cards have helped us a lot in this area. Brute-force password-cracking boxes used to have to be supercomputers, then they had to be weird things built out of ASICs and FPGAs at universities and intelligence agencies. Now you can create rainbow tables or ignore them entirely and just brute-force from scratch with a normal PC and a few midrange graphics cards, or a box full of said cards if you're fancy.
If you've got a handy botnet to do your bidding, things become even easier. (I wonder if any of you clever little monkeys have used Amazon's EC2 cloud computing system to attack Amazon accounts?)
What's really great, though, is how much both users and operators of passworded Web sites help us out.
Users are often required to use their e-mail address as a username. And they also, delightfully, tend to use the same password for multiple sites.
So when one site or, oh I don't know, the whole Gawker network, leaves a huge pile of hashed login data lying around where one of us can find it, or when idiots like RockYou.com let loose a giant pile of plaintext passwords, we've now got a good chance of being able to log in as those same user-names, using those same passwords, in various other places.
If a user only uses duplicate logins on unimportant sites, then it's not much use to us. Cracking someone's accounts on IMDB and The Pirate Bay and BrickSet only let you give every Rob Schneider movie ten stars, leave adulatory comments about torrents of Belgian cuttlefish pr0n, and say you really wish Lego would bring back Fabuland.
If a given person's login to comment on a poorly-secured crocheting blog is the same as their login for PayPal, though, we're in business!
The big password leaks are great for us in another way, too: They let us see the kinds of passwords that people like to use. This means huge swathes of the brute-force password space can be left to the if-all-else-fails very end of the cracking process. We've now got giant dictionaries of actual passwords, and heuristics to mutate them into other likely candidates, which we can use before slow brute force.
If you're happy with cracking only a quarter of the accounts you attack, you can now get it done before your laptop battery goes flat. (Then later you can brute-force a few of the hard ones, to see if there are more patterns to be harvested!)
I'd especially like to congratulate those among us who, clearly, are responsible for almost all online "password strength tester" sites.
Your average schmuck thinks those sites may actually save the passwords people type into them, for later misuse. That's possible, but terribly unimaginative. These sites' real purpose is, of course, to give good ratings to terrible passwords, like "jamesbond007".
Howsecureismypassword.net says jamesbond007 should take "37 years" to crack. Passwordmeter.com says it's "Good". Testyourpassword.com and Microsoft's checker here both say it's "Medium". Testyourpassword.com actually has a "Common password!" warning feature, but doesn't reckon jamesbond007 warrants it.
The checker at Online Domain Tools has a dictionary-attack function. You have to click a button to use it, but if you do then it'll note that "passw0rd" is guessable because it's just a leet-speak version of "password". This basic level of password-checker functionality is, thankfully, rare.
(One of you busy little bees has probably also made sure your password-cracking dictionary-permutator takes into account that most brilliant password obfuscator that everybody thinks they're the first to have thought of, typing a simple password with fingers offset by one key on the keyboard. Converting "snoopdogg" into "dmpp[fphh" that way will slow down one of us professional miscreants about as much as sticking the Post-it with your password written on it to the underside of a drawer. Or hiding your drugs and money in the toilet cistern, for that matter.)
The Online Domain Tools dictionary-checker also flags "jamesbond007", because both "james" and "bond007" are in its dictionary. It still evaluates the password as "Medium", though. Oh, and it also warns if you've picked one of the top ten thousand passwords (from this list, I think).
On the other hand, though, my Reddit password might be, but isn't, "iki37nnplq". The Online Domain Tools dictionary attack checker thinks that's unsafe because "iki", "nn" and "plq" are all dictionary words. This may be the case, but only if your dictionary contains a large number of two- and three-letter strings that do not resemble actual human words.
(Further exploration of this phenomenon with five pseudorandom-generated - not just mashing-the-keyboard - strings of ten letters was similarly amusing. "ZfXdSXZRco", "iZBPOYLdiQ" and "fNyUTeIZGJ" all rated as "Safe!", but "ZfXdSXZRco" and "yKRmKiXiNR" were both "Not safe!" on the grounds of containing three dictionary words. In the latter case, two of the dictionary words were alleged to be reversed. They were, of course, the well-known words "RNiX" and "RKy".)
The accurately-titled Yet Another Password Meter says jamesbond007 is "Very Weak", but only because it lacks upper-case letters, symbols, and symbols in the middle of the password. Rectify those mistakes by changing it to "Jame$bond007" and now it's "Strong"! Online Domain Tools reckons "Jame$bond007" is "fairly good", with no warnings at all.
Great work, guys! Thanks!
But then there's the Password Strength Meter at My1login.
Those of us who very much like it when people use terrible passwords should probably do something about this site.
It's quite concerning.
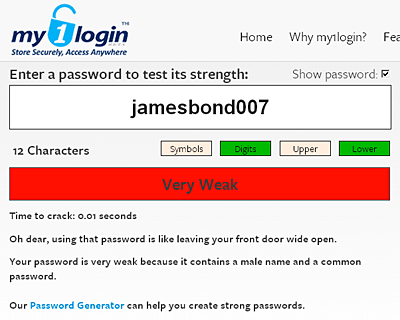
My1login correctly, but highly alarmingly from the computer-criminal point of view, says "jamesbond007" is "Very Weak":
And just changing it to Jame$bond007 doesn't help!
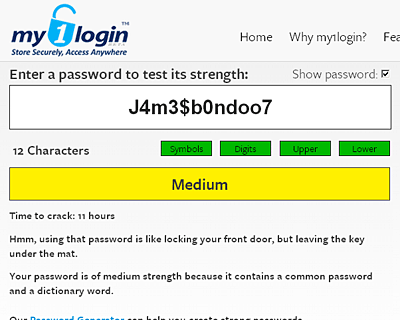
What if you totally leet it up, with "J4m3$b0ndoo7"?
Now it's "medium", time to crack 11 hours, which is again annoyingly accurate.
(You can go further in leet-translation, but once you start getting into "/\/\" for "M" and symbol characters, passwords become too hard for our victims to type.)
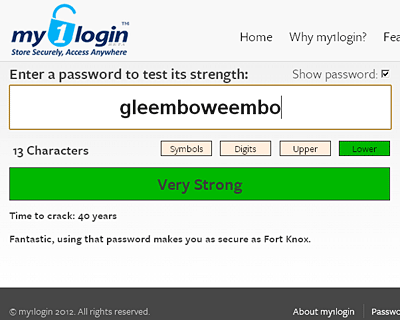
Let's try a memorable nonsense word, "gleemboweembo":
"Very Strong". As indeed it, cursedly, is.
My1login's irritating reliability continued when I tried "vingospib" - that got a "Medium", because it's not very long. Then "golobowobs" got "Strong", because it's longer. Trying "mysupersecretpassword" resulted in a "Very Weak", "because it contains a dictionary word and 3 common passwords".
We can't even try to overload the My1login tester by feeding it very very long passwords, because it seems to do its computation on the client side. Super-long passwords will give your browser a lot to think about, as the "time to crack" number becomes more and more outrageous. When I tried an extremely sensible password composed of 229 characters of keyboard-mashing, for instance, it scored a time-to-crack of "515 billion trillion trillion trillion trillion trillion trillion trillion trillion trillion trillion trillion trillion trillion trillion trillion trillion trillion trillion trillion trillion trillion years". And you can keep on typing if you like. (I don't know what the ceiling password length is, but 500 words of Lorem Ipsum made it unhappy.)
Is My1login's Password Generator just as good, my fellow criminals may mow be worrying, or does it generate impossible-to-remember character-salads that are only any use if you're using a password-management service like, for instance, My1login?

Ah.
Well, at least there's that.
(A gratifyingly large number of Web sites also still give us that most invitingly wide-open of back doors: Password-recovery "security questions" that are a matter of public record.)
Nonsense words like "Pingoflorble", and multi-word passphrases with no fancy substitutions like "speaker cup cable junction" or the famous xkcd "correct horse battery staple", are easy to remember, moderately easy to use and damn near impossible to crack.
Fortunately, to a first approximation, nobody uses them. So we don't have to worry.
We're like burglars passing over the place with the window-bars and alarm stickers in favour of kicking through the fibro next to the security door of the house down the road.
As long as most users stick with fibro walls, other people's identities will continue to fund our lavish lifestyles.
And now, friends, it's time for the traditional Courvoisier drinking competition. And then perhaps a little Lambo racing!