Windows vs Linux vs SnapGear:
A Connection Sharing Odyssey
Review date: 17 October 2001.
Last modified
03-Dec-2011.
The notion of a "home LAN" - a Local Area Network (LAN) in an ordinary house, or even a normal small business - used to be preposterous.
Less than ten years ago you needed whole special operating systems to run a LAN, and the hardware was expensive, and the setup took ages, and what were you going to do with it, anyway?
At that time, the idea of even having an Internet connection, much less sharing it among multiple computers in the one house, was similarly silly for regular people. When Windows for Workgroups 3.11 came out, which is pretty much the point where normal humans were starting to find it possible to put together a basic LAN, there were still only about 1000 servers on the World Wide Web, if that. E-mail, pirated software and smut you could get from Fidonet bulletin boards (or from CompuServe or AOL if you were richer and less hip). Consumer ISPs didn't really exist yet.
OK, OK, I'll stop writing as if I'm being paid by the word. This page is going to be long enough anyway.
Nowadays things are different, and lots of people have Internet access, and it's easy to network computers, and thus the ability to share one dial-up or always-on Internet connection across your little home or small office network is something people want. For this reason, every version of Windows since Win98 Second Edition (which, as we all know, includes seven minutes of previously unseen footage) has included Microsoft's inventively titled Internet Connection Sharing (ICS).
I've been using ICS for a fair while. For about as long as Windows 2000 has existed, in fact, because I sure as heck wasn't going to make a "network appliance" out of a Win98 computer.
I've got an always-on cable Internet connection, and it sort of defeats the purpose if you connect an always-on Internet link to your LAN via a computer running an often-broken operating system.
It took quite a long time before people found out that Windows versions 95 through 98-pre-SE were physically incapable, as standard, of running for more than 49.7 days without crashing. Seriously.
And the reason it took a while for that discovery to be made was that something else is very likely to have pole-axed a Win95-series operating system before it's been running that long.
So Windows 95, 98 or ME is not the operating system of choice if you want to build the sort of server that you can safely wall up by accident. That's the reliability you want from an Internet-sharing box.
Windows 2000, on the other hand, is up to the task.
On OK hardware, even if you're running lots of applications all the time, Win2000 can reasonably be expected to give you weeks, if not months, of uptime. On a computer that just sits there quietly without a monitor and does network-appliance tasks, Win2000 should behave itself forever or until some hardware fails, whichever happens sooner.
Here's what you do to turn a Windows 2000 box into a half-way secure Internet sharer. I tell you this for compare-and-contrast purposes, because we'll be having a look at a couple of alternative strategies in a moment.
First, you attach your dial-up modem to it, or install a second network adapter if you've got a broadband connection that needs one.
Second, you do whatever's necessary to get the 2000 box connected to the Internet, as if you wanted it to be a stand-alone machine.
Third, you make sure that File and Printer Sharing, if it's installed, isn't bound to whichever connection you're using for the Internet link. If it is, then the computer's inviting everybody in the world to have a rummage around in its underpants. If it isn't, it isn't. I still wouldn't bet a mint copy of Action Comics No. 1 on the Win2000 PC being immune to the attentions of the l337 h4XX0rZ of the world, but if you don't fall victim to any dumb e-mail trojans or otherwise compromise its security yourself, it'll do for domestic purposes.
Fourth, you go to the properties for the Internet-linked network connection, and you go to the Sharing tab, and you click the box that turns sharing on.
Now, any computer that's connected to the same LAN as you've hooked up to the non-Internet network adapter in the sharing box can just be told to get its TCP/IP settings via Dynamic Host Configuration Protocol (DHCP), because ICS provides a DHCP server as well as Network Address Translation (NAT) connection sharing, which requires no special setup on the client machines.
Now, assuming you had a working TCP/IP LAN in the first place, that LAN is on the Internet. Reboot everything in sight so that the client machines know about the new server, and you're done. That's it.
OK, it's not exactly a two minute job, but it's not like writing an MMORPG or anything.
If you want in-depth configurability, then ICS is not what you want to use. But for most people, it's great. And it's greater, now that Windows XP's lumbered onto the scene; ICS in XP is considerably more capable and configurable.
The down side of this idea is, of course, that using a whole darn general purpose PC running a giant expensive commercial operating system to just share your Internet connection is a bit like using a Bentley to plough a field. Or, indeed, like using a jet engine to cool your beer. Except, unlike these two analogies, the Win2000 Internet sharing option really is pretty simple and effective. And it's free, if you happen to have already paid for the computer and the OS.
You can get a bit more value out of a Windows sharer box by using it as a print server and even as a file server as well, if you like. That's not the world's most secure solution, but we've been over that already, and ICS in XP has what is at least described as a firewall. Who knows. It might really be one.
Even Windows 2000 Workstation has simple TCP/IP filtering built in, which blocks all incoming connections on a given network adapter, except for whatever ports you specify. Add a blood-pressure-raising log of every attempt to connect to your computer on a port on which you're not running a server, and you've got the core feature set of commercial "Personal Firewall" software, right there.
The way a lot of Windows sharer machines get set up, of course, is on a computer that's already being used for something else, commonly as someone's workaday machine, and which is running a pirated copy of Windows. Which reduces the outlay considerably, as a combination of parsimony and crime is often likely to do. That doesn't make it right, but anybody whose product competes with Microsoft software has to bear in mind that, a lot of the time, they're competing with pirated Microsoft software. Pirates don't care about the high retail prices of the big Microsoft OSes. Or maybe they do, and that's why they pirate them. Anyhow, they're not paying.
If you are paying, you might want a cheaper solution.
You might also want a more elegant one.
If someone's doing ordinary computer tasks on your sharer box all the time, then their activity can have an impact on other people's Internet connection if they manage to get the computer to flog itself witless. And anything they do that requires a reboot (voluntary or otherwise...) will of course interrupt everybody else's online fun. There are more than a few other Internet sharing software packages for Windows, many of which are superior to ICS in several respects, but none of them solve these problems.
If you want to do what Windows connection sharing software does, and more, there are two basic alternatives to using a beefy expensive PC and a big fat Microsoft OS, or a really big fat Microsoft OS, really really big fat Microsoft OS, or an astoundingly big fat Microsoft OS.
Alternative option one is to use one or another free Unix variant, which will run more than fast enough for Internet-sharing purposes on very elderly (and thus cheap) PC hardware.
Unix, in all of its flavours, is The TCP/IP Operating System. It does TCP/IP network appliance stuff in much the same way that Ash does zombie-killing. For comparison, on old hardware that's plentifully powerful enough for Linux, Windows will do network appliance stuff in much the same way as Piffany does naughtiness.
We'll come back to the subject of Linux/*BSD/whatever on an old PC in a moment. And you will share my pain, I promise you. Oh yes. You will.
The second alternative option for Internet sharing is to use a dedicated small-plastic-thing-powered-by-a-plugpack. More expensive than an old PC, but much simpler to get going. And substantially cheaper than a new PC and copy of Windows.
There are lots of these Internet "sharer" or "router" or "gateway" products, and all of the recent ones have similar feature sets. They do NAT. They do DHCP. They may do other tricks, or they may not. You can get basic models for less than $US150.
Here's one that's more capable than usual. It's SnapGear's LITE+ Internet Access Device.
The basic SnapGear product, the "LITE", costs $AU499 from SnapGear dealers here ($US249 from dealers in the States). The LITE+ has a built in four port 10/100BaseT switch, and costs $AU599 ($US299).
In the documentation, SnapGear refer to their box as a "SnapGear VPN Router" a lot. This is because this is not your normal NAT-plus-DHCP sharer whatsit; it does Virtual Private Networking (VPN), as well.
Essentially, SnapGear's aim seems to be to provide something that's as easy to set up for basic functions as the simplest of the plug-and-go Internet sharer appliances, but which also provides various of the extra connectivity functions that you're likely to want from a Linux or *BSD box. The SnapGear routers aren't complete replacements for a PC Unix machine - you can't add more network interfaces to them than they come with in the first place, for instance, and you can't run extra software like a caching proxy or a mail server. But, within their limits, they behave like a normal stand-alone Linux box, except they're a lot easier to get working.
That's the idea, anyway.
To test the theory that the LITE+ would make sharing a Net connection as easy as the ratio between a circle's diameter and its circumference and substantially easier than any other similarly capable solution, I set out to do exactly what I've always told people, based on no personal experience, was the alternative to dropping at least a couple of hundred Australian dollars on one of these dedicated sharer boxes. I got myself an old PC, and I installed a plug-and-go Linux sharer/firewall package on it.
The problem many people have with doing this themselves is that setting up an old PC with a pair of network cards to share their broadband access is harder than setting up a new PC the same way. They're probably not too confident about doing that, so wrestling with a wrinkly old Pentium or 486 doesn't turn 'em on.
But you don't need to be a Linux guru to make one of the pre-packaged Linux router distributions work. And it's cheap. And lots of people who don't really know one end of Unix from the other have managed it.
Using a port of Csh on my Amiga was all I knew about Unix, but how hard could it be?
Too hard, as it happened.
But, at least, my experience served as a perfect object lesson in why you might want a little $US250 plastic box instead of a $US50 old PC to do a job like this.
[Expletive deleted] FreeSco
FreeSco is the punny name (it's like a Cisco router, except it's free...) of one of the several super-small Linux distributions made to let people turn old PCs into network appliances. Like all of the other such distributions, it's a free download. All you need is a PC to run it on.
The price of that PC can vary from nothing (if you've got a 486 with everything you need mouldering away in a cupboard already) to not much (if you need to scrounge up a couple of extra components for an old PC), to not a lot more than not much (if you need to buy a whole new old computer).
I was in category C, so I headed off to Auction Trader, an outfit here in Australia that generally has plenty of stock of old business machines. Auction Trader is a lousy source for anything particularly new, thanks to numerous turkeys who bid such things up to preposterous prices. But they regularly get in lots of old Pentium-class machines, and check them out, and package them properly, and deliver promptly. In my experience, at least.
I paid a hair over $AU70 (about $US35) to have this item delivered to my door in a cocoon of bubble wrap. It's a 90MHz Pentium Compaq Prolinea 575 with 32Mb RAM, keyboard, six hundred and something megabyte hard drive and one Intel ISA Network Interface Card (NIC) already installed. For the price of three bottles of medium-quality gin. But, unlike 2.1 litres of spirits, this thing can run Doom.
I needed another network adapter, so I bought the finest, cheapest PCI NIC I could find. Which, for those of you who follow the pricing of these things, was inexpensive enough that I can only surmise that basic PCI 10/100BaseT network cards will shortly be sold for the purpose of scraping mud off boots.
This computer was now perfectly adequate to run FreeSco - rather overqualified, actually. But I had to be clever. See, I was looking for something I could do with this:
This is the VME Systems CF-IDE CompactFlash IDE adapter which I review here. It lets you take a CompactFlash card and use it as a normal IDE device, which you can plug into a regular motherboard. All CompactFlash cards can run in ATA mode; the adapter's little more than a connector-converter.
A basic "Solid State Disk" (SSD) like this is just the thing for a computer which you don't want to boot from floppy (FreeSco is small enough to do that, but floppies aren't renowned for their reliability) or from its aged hard drive (I've got no illusions about the reliability of hard drives made by companies that haven't existed for more than five years).
And small capacity CompactFlash cards aren't hard to find. I got the 8Mb one in this picture for nothing from a friend who got it with their digital camera, as have so many other people. Said friend has since purchased a card that can hold more than five full-quality images.
Out came the Prolinea's hard drive...
...and in went the CompactFlash alternative, attractively insulated from the computer chassis with gaff and double-sided tape.
If I wanted to run any operating system that needed to use virtual memory (hard drive space used to augment physical RAM), this would be a terrible idea. Flash RAM, as found on memory cards, can't handle zillions of read/write operations, which is what it'll get if it's used as scratch space. But this computer had quite enough memory that FreeSco wouldn't need to be set up to use any swap space, and I sure wasn't installing Windows on an 8Mb "drive".
Now it was time to play The Old Compaq Game, and remind myself that brand name computers not only generally suck right now, but have generally sucked for some time.
Want to get into the BIOS setup on a Prolinea 575 to make sure its new network adapter (installed in its one, count it, one, PCI slot) and 8Mb drive are happy? Just press Delete or F2 or something during startup, right?
Wrong!
It's F10, and you press it during startup, but that won't do anything unless you've got a special Diagnostic Partition on your hard drive. You can make the partition by using a couple of floppies, setup programs for which you can still download from Compaq's site. The floppies can also boot you straight to diagnostic mode.
I couldn't make a Diagnostic Partition on my little SSD, but I could waste small but significant slices of my life booting from the floppies numerous times, which is what I did.
Once I'd made sure the NICs weren't trampling on each other or anything else and the new "hard drive" was recognised - which was all pretty easy, really - I turned to my FreeSco setup disk.
After I figured out that a boot failure with a "can't stat directory" error was happening because I'd write-protected the disk, getting FreeSco installed wasn't that hard. Compared with genuinely hard things. Like climbing mountains. I say that now, anyway.
While I was doing it, I found myself taking deep breaths, partly because it's easier to say a really satisfying string of rude words when you've breathed in completely, and then reminding myself that Linux isn't really wilfully, hideously, militantly user-hostile. It just seems that way when you're a puny Windows user spending two hours trying to figure out how to copy three gosh-darned files off a confounded floppy disk and into a dad-blamed directory you can't ye-gods-and-little-fishies find.
I typed that last sentence while I was wrestling with that problem. I've edited it a bit for publication.
I needed to tweak the FreeSco install because the ISA network card I had wasn't covered by the stock FreeSco driver modules, and I had to install another one from the extra modules pack. Three could conceivably apply, so I copied over all three of them. No reason not to, with the vast expanse of an 8Mb CompactFlash card to work with.
Once I'd done that, I went through the quite straightforward FreeSco setup procedure.
And then I did it again.
And again.
And again and again and again and again.
Because, as it turned out, the FreeSco module for the ISA network adapter I was using, an Intel Ether Express PCLA8225 using their 82595TX chip, didn't work.
The cheapo Skymaster PCI NIC I'd just added was A-OK, but the Intel one was a non-starter, and the result was an eternal "waiting for dhcpoffer" problem that could have had many other causes, all of which I explored before posting to the FreeSco support board about the problem.
Much un-plugging and re-plugging of the Win2000 sharer box happened during this period. Also much cursing.
Much more cursing, rather.
No help came from the FreeSco board habitues, except for the observation that verily, the module for that network card would appear to be exactly as good as Microsoft would like you to believe all free software is.
So I put the Linux box aside.
I could have gone on to try LRP or its spin-off Coyote, both of which are floppy-sized distros with the same basic aim in life as FreeSco. I couldn't install the popular SmoothWall without swapping the hard drive back in, or getting a bigger CompactFlash card, but that wouldn't have been a big deal.
But I still had my 400MHz Celeron Win2000 box, which had continued to use its ridiculously large muscles to do its ridiculously small job with perfect aplomb whenever I asked it, during this whole cursed episode.
And then the SnapGear LITE+ arrived.
Frankly, I felt I'd done my darn duty as far as Linux-tweaking went. I'm sure FreeSco and its relatives are great, when they work with the hardware they're supposed to, and I'm not for a moment suggesting that Windows boxes can't be every bit as frustrating, not to mention much more expensive. But when something's officially labelled "insanely easy to set up", I reserve the right to direct long and creative streams of colourful Anglo-Saxon expressions at it and at its creators when that description proves to be completely inaccurate.
On to the little plastic thing.
Snap!
SnapGear's LITE+ is about 42 by 180 by 123 millimetres (1.65 by 7.1 by 4.85 inches) in size. It doesn't weigh much. It's got lights on the front...
...and ports on the back. From left to right, the DC power input, the RJ45 10BaseT "WAN" port for connecting a broadband adapter, the serial port, the Erase button that resets the router to its factory defaults (if you've forgotten your password but want to change some settings, this is the button you'll have to press), and the four 10/100BaseT switched LAN ports.
The whole LITE+ kit I received includes the power supply, one CD-ROM, and a couple of RJ45 network cables. The documentation is all on the CD in Adobe Acrobat format.
Inside the LITE+ there's just this one circuit board. Some cheap network appliances contain components that get hot enough that they can't rely on passive convective cooling, and have to have a little fan or two. This is bad, because little fans - especially cheap sleeve bearing ones - wear out pretty quickly, and also because these gadgets commonly run from five volts, and so have five volt fans, which you can't buy in the average computer shop.
The LITE+ has no fan. It runs a bit warm, but far from alarmingly so.
Here's part of the reason for that. The CPU in this thing is a 66MHz Motorola ColdFire XCF5272VF66, whose typical power consumption - and heat output - should be down around half a watt. This CPU scores a BogoMIPS rating of about 43.8, according to the LITE+'s diagnostics.
The LITE+ runs the ColdFire port of uClinux. "uC" is commonly used as a plain-ASCII pseudo-abbreviation for "microcontroller", because "u" looks pretty much like the Greek letter micro, "µ". uClinux is the Linux port for processors without a memory management unit, which is something that all ordinary personal computers now have, but which wasn't common in the olden days, and didn't exist in the earlier Motorola 680x0 CPUs. They survive today as the core of various microcontrollers, including the ColdFire and the Dragonball processor used in Palm organisers. Microcontrollers differ from plain CPUs because they've got extra knobs on - in the 5272 ColdFire's case, an Ethernet controller and a USB module.
Got that? Good.
The choice of uClinux for this gadget isn't all that amazing, seeing as uClinux is being developed by a company called Lineo, and Lineo own SnapGear.
Helping out with the LITE+'s network ports are this Realtek RTL8305S five port 10/100Mbps Fast Ethernet Single-Chip Switch Controller...
...and this Davicom DM9008 ISA/Plug and Play Super Ethernet Controller.
The whole idea of a one-box Net sharer, of course, is that you need have no comprehension whatsoever of what's under the lid. I like taking pretty pictures of chips, though. Nyaah.
Setting up
Out of the box, the SnapGear router doesn't have a fixed IP address. It's set up as a DHCP client on the LAN (as opposed to WAN) side, so if you just hook it up to a network that's already got a DCHP server running, it'll get an IP address that way.
I was switching over from ICS, though, and the DHCP and NAT functions in Win2000 ICS are one lump; you can't have one without the other. Well, OK, there's probably some way to turn off NAT and leave DHCP running by tweaking some registry entries or something, but I wanted the LITE+ to take over both jobs anyway. Which meant it needed a fixed IP address.
To give it one, you have to hook it up to your network and run a special application.
Most of the SnapGear models connect to a 10/100BaseT network with a plain straight-through cable, which goes from any normal port on a hub or switch to the one "LAN" port on the router. The LITE+ I got for review, though, has to be "cascaded" into the network like any other switch - so you connect any of the LITE+'s LAN ports with a crossover cable to a normal hub/switch port on your LAN, or you use a straight-through cable to connect the LITE+ port to an "uplink" port on a hub or switch.
The LITE+ connection process is easy enough to do for anybody who's ever connected hubs or switches together before, but it's not mentioned in the documentation, which is very good in some areas but could do with a brush-up in others.
The standard SnapGear install CD comes with Windows install software on it, because that's the big market, of course. Linux users, however, don't have to run Windows to give a SnapGear router a static IP. In the CD's "tools" directory, and available on SnapGear's site here, is an x86-Linux setup executable.
The above link is the download page for the latest firmware updates, PDF documentation and so on as well, by the way.
All the setup software does is find the router on the LAN and let you assign it a password and IP address, which has to be on the same subnet as the computers on your LAN that you want to be able to see the router. The setup program sets the first three numbers in the IP address the same as they are on the host machine, which makes this easy enough.
After that, most SnapGear router users will do the rest of the configuration via the router's "Web page" interface. As is normal for these appliances now, you can just look at the router in a Web browser with the address http://[the router's IP address], and you'll get...
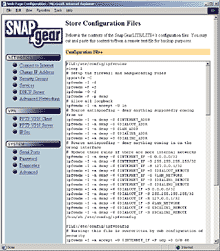
...this sort of interface.
This picture shows the router's config files, which'll make sense to Linux users; this simple HTML form lets you copy and paste all of the text for backup purposes. You can also edit individual files, from another page. But ordinary users shouldn't have to do either; all of the configuration you're likely to need to do, including things like VPN and firewall setup, can be done from other click-and-go interface pages.
Command line enthusiasts can connect to the SnapGear router via telnet. This lets you do everything you can do via the Web interface, plus some extra low-level stuff, and extra trimmings like setting the router's clock. My review router thinks it's the second of December, and I haven't bothered changing that, because it has no effect on anything important. This is reflected in the fact that the LITE+ has no proper real-time clock; turn it off and on and it'll reset its clock to whatever time was saved to its flash memory.
You can, of course, set whether the telnet and/or HTTP setup interfaces are accessible from the Internet (they're password protected, naturally), or just from the LAN.
The LITE+ makes it quite easy to set up the basic router function - making an Internet connection, and sharing it. If you've got a dial-up, ISDN, cable or xDSL Internet connection, the SnapGear box should be able to deal with your ISP's oddities.
What kind of oddities are we talking about, here?
Dial-up ISPs are all fairly similar, and the SnapGear box has the features you'd expect. Dial-on-demand, a configurable and disableable idle time-out, automatic disabling of dial-in server functions (of which more later) if you set the modem to be used for Internet access, and so on.
Broadband providers can be trickier. Different broadband ISPs use different authentication systems. Here in Australia, for instance, there are only two major broadband options - Optus@Home (now wholly owned by Optus, who took it over from the ailing @Home), and Telstra's BigPond services.
I use Optus@Home's cable service, which has - or, at least, had - the standard @Home authentication system.
The way this worked when I signed up was simple enough. Every user's given their own "computer name", which is what they have to use on the broadband-connected machine. When you give your computer a name in Windows' Network Identification, you're setting both your NetBIOS hostname and DHCP host identifier to whatever that name is. Other operating systems, like MacOS and the various Unix flavours, separate these two things - you can have a computer with an @Home-style "co1234567-a" sort of DHCP identifier, and a more readable NetBIOS name. But in Windows, it's all one lump.
The DHCP identifier worked like a username and password rolled into one for @Home networks; when a device asked one of @Home's DHCP servers for an IP address, it sent the identifier, and if that identifier was one that was meant to be connected to that part of the @Home network, its request would be acknowledged.
Without the right DHCP identifier, you couldn't connect. And, conversely, anybody else on your network node (which can be quite large) who knew your hostname could pretend to be you and deny you service. They couldn't use up your bandwidth allowance, though, because that was, and is, tied to the MAC address of your cable modem. The MAC address is a (theoretically) unique 48 bit number that identifies every Ethernet network adapter, and which you probably don't even know.
@Home can detect such shenanigans by looking for mismatches between DHCP identifiers and MAC addresses, and then they can cut off service to the offender's cable modem, no matter what name he uses.
Every half-decent Internet sharing box these days can be configured with a DHCP identifier, and so can the SnapGear LITE+. It actually has explicit support for Optus@Home; there are different versions of the SnapGear products for different countries, and the Aussie edition of the LITE+ which I got for review gives you only three options when you tell it to use a cable Internet connection. There's a "generic" set-it-up-yourself option, plus one option each for Telstra and Optus.
The way Optus@Home works now, though, is apparently different. Now, the cable modem MAC address is everything, and nothing else matters. The head-end router that's the first to know about your DHCP request tags it with the MAC address of your cable modem, which is the unique identifier used for traffic reasons already. And your hostname can, apparently, be whatever you like. You can set it to the special co-123blahblah name if you want, or you can call your computer Popocatapetl007; it doesn't matter.
Some other broadband ISPs authenticate by the MAC address of the network adapter connected to the cable modem, not the address of the cable modem itself. ISPs that use this system log the address of the network adapter they gave you when you signed up; if you use any other network adapter, it worketh not. A dedicated sharer appliance counts as "any other network adapter", here.
The SnapGear routers have a configurable MAC address, though. You have to use the Telnet interface to change it, but it's easy enough to do, and in the manual. So all you have to do is know the address you're meant to have (download the diagnostic software for your NIC and it ought to be able to tell you, if it's not obligingly on a sticker somewhere), and then change your SnapGear box to match.
If you've got a DSL connection of some flavour, you're likely to find yourself using Point-to-Point Protocol over Ethernet (PPPoE), which requires you to run client software on your PC to connect. ISPs have a tendency to supply lousy PPPoE software. Thankfully, the SnapGear router speaks PPPoE, and should remove this problem.
If your ISP requires you to manually enter DNS and gateway addresses when you connect, you'll need to do so when you set up the SnapGear, too. The manual implies that this is something you'll always have to do, which will puzzle Optus@Home users, because on this service everything just works by DHCP magic and all you need set up is the special identifier - and, it seems, not even that any more.
One other thing, which irked me considerably when I was trying to get the LITE+ connected, was that it didn't. It did everything fine except actually allow computers attached to the LAN to access anything on the Internet. It got settings via DHCP from the ISP, it provided DHCP services to computers on the LAN, its setup pages all behaved themselves, but it behaved like a firewall that had "failed safe" and blocked access to everything.
Which, as it turned out, is exactly what it had done. Because of what SnapGear told me was a "timing issue" (which I'm practically certain is one of the BOFH excuses), the router had bolted its doors and hunkered under the kitchen table with a shotgun.
I speak metaphorically.
Fortunately, there was a workaround - I just had to go to the "Services" setup page and click an "Apply" button without making any actual changes. This re-ran the firewall rules and fixed the problem.
SnapGear now have a new 1.43 version of the LITE+ firmware available on their download page, which fixes this problem. The Windows "Netflash" executable firmware updater is very easy to use.
People who've flashed their motherboard or video card BIOS will know that interrupting a flash upgrade is Very Bad, and that's the case here, too. There is, fortunately, no reason to upgrade every time an upgrade's available; only when a change fixes some bug that bothers you - like this one - or introduces some new feature you want, is it necessary.
Extra features
If all you want is DHCP and NAT, there are lots of cheaper products than SnapGear's that do it. The SnapGear routers cost more for a reason.
If you want configurable port forwarding, to forward packets from the Internet to a computer on your LAN that's behind the router and so doesn't have a valid Internet IP address, the SnapGear boxes can do it. If you port-forward an internal HTTP server, it'll take over from the router's remote-administration server and make it impossible for remote users to access the router admin pages, because you can't change the port the router's own HTTP server uses. But apart from that, the forwarding's fine.
Any number of TCP or UDP ports can be forwarded to whatever internal machines you like, but you have to set each one up individually. A fair few other routers can do this as well.
Another SnapGear feature that's not unknown on other better-than-base-model routers, but is done well by the SnapGear box, is configurable access control and port filtering - setting the firewall to stop particular services from being accessed by particular users, so you can lock out Web access but leave e-mail, for instance. You can the access policies separately for dial-in and LAN users as two groups, and you can also set policies individually by IP address for each computer on your network.
One thing the SnapGear router lacks is access-attempt alerts, which are a big, if not very useful, feature of personal firewall software.
There are valid reasons to want to know what attempts to compromise your network security are being made and when, but I don't think it's much of a limitation that the SnapGear routers won't tell you.
If you're microsoft.com or cia.gov, you want to know who's trying to hack you. If you're that big, in fact, the small vulnerabilities of various firewall platforms are serious enough, given the number of enthusiastic crackers banging on your door all day, that you should run a multi-layer heterogenous firewall made up of systems using different architectures and different OSes.
If you're a home or small office user, though, then unless you've just invented antigravity or are plotting to kill the President of the United States, one level of firewall should be more than adequate. And there's no need to worry about attempts to probe your network.
You don't care if someone flipped the door handle of your parked car, found it locked, and wandered off, after all. Neither should you care if someone probed your Internet connection, found no vulnerability, and went away. People who run commercial Windows firewall software on PCs connected to the Internet commonly get needlessly excited over the endless NetBIOS and Trojan-server port probes, and similar evidences of hopeful script kiddies on the prowl. There's no real reason for most people to care about this sort of thing. Nobody can make a peephole in your bathroom wall by just staring at it, no matter how hard they try.
A shortcoming of the SnapGear router that might matter more to some users is that it has no "DMZ" feature, so you can't make one computer on the LAN accessible from outside, as if the router weren't there. The other features let you make most services work, but if you've got something that just can't be made to operate through the firewall, you're stuck with it, unless you do something gimcrack like running it on a two-network-adapter box that's physically between the router and the Internet connection and, itself, sharing the connection through to the router. I guess that'd work. Perhaps I guess wrongly.
Want to run a dial-in server? You can, but not with the LITE or LITE+. These two routers only have one serial port, which can be used for dial-up Internet connections only - including ISDN. The more expensive SOHO+ and PRO routers have twin serial ports, and you can use one for Internet access and one for dial-in, if you like, or use both for dial-in connections. These two routers let you run a standard RAS server, and also support RADIUS/TACACS+ authentication. Dial-in users can have access to your LAN as well as to the Internet via the router.
If you're looking for censorware-ish or activity-tracking features, the SnapGear routers don't do that either. You can't ban access to particular Internet resources by IP or by content, and you can't see which computers on the LAN are doing what. You also, by the way, can't tell whether someone else is doing administration tasks on your router at any given moment. This is a small security concern - use a sensible password and don't tell people what it is and you're safe, even if you do let the general Internet access the router's setup - but it's more likely to be a problem if two people are changing things at once, resulting in two-birds-pulling-different-ends-of-the-worm annoyances.
The major selling point for the SnapGear routers, though, and something that few other consumer routers even try to do, is...
VPNs
In a Virtual Private Network, traffic from a remote network node "tunnels" to your LAN via another protocol, which encapsulates and encrypts the traffic so that eavesdropping isn't possible, and so that protocols that can't normally be routed over the Internet - like IPX/SPX - now can.
The result is a connection that's somewhat slower than you'd expect from the bandwidth of the Internet link, but secure. It looks, from a user's point of view, not unlike a somewhat limited part of the LAN.
SnapGear's VPN implementation doesn't support Windows network browsing, so Network Neighborhood (or whatever your flavour of Windows calls it) won't show remote machines. But you should always be able to connect to them by going to Start->Run and entering
\\[IP address of remote computer]\[name of shared resource]
So, for instance, if there's a shared directory called "files" on a box on a VPN-connected remote LAN that has the IP address 192.168.0.128, typing "\\192.168.0.128\files\" will get you a window containing that share's contents.
You can map drive letters to shares, assign them shortcuts on the desktop, and use other protocols across the VPN as you wish. Which lets you, for instance, play multiplayer games that don't have an Internet-connect capability with friends in distant places. That's not a goal you're likely to want to spend big bucks to achieve, but it's a simple demonstration of what VPNs make possible.
SnapGear's routers can work as PPTP VPN clients or servers, so you need no client or server software running on any computers at either end of the tunnels. Other cheap "VPN-capable" routers just don't block VPN traffic from computer-hosted VPN software; SnapGear's boxes do the job themselves.
The SnapGear routers support both Internet Protocol Secure (IPsec, using FreeS/WAN) and Point-to-Point Tunneling Protocol (PPTP) and seem to be pretty much buzzword compliant to me. All authentication levels from none to MSCHAPv2 and RC4, simple enough setup (which is not something you'll necessarily get from Windows, wizards or no wizards), and up to five simultaneous PPTP tunnels or 12 simultaneous IPsec tunnels, even on the LITE+. The plain LITE supports only four and 10 tunnels, respectively, and the top-end $AU999 ($US549) PRO model supports 40 and 70, respectively. For home and small office purposes - including working-from-home purposes - either LITE flavour is more than adequate.
Basically, unless you want to connect to some peculiar proprietary VPN, this box should be able to do it. It can work as client or server for PPTP, and it ought to work with all of the popular hardware and software VPN systems, from the built-in software that comes with Windows to big expensive corporate appliances.
Client and server aren't relevant terms for IPsec purposes, by the way; IPsec is just an authenticity/confidentiality assurance system at base. When someone calls something an "IPsec server", they really just mean it can handle a ton of IPsec traffic without bogging down on all of the encryption.
You do not need a SnapGear appliance administering the Internet connection of everybody that wants to participate in your VPN. But if you want the nearest thing to a plug-and-go system that you're likely to find, SnapGear boxes at each end of each link look likely to give it to you. The SnapGear PRO router should be adequate for quite serious corporate applications.
This is quite a big deal.
You see, it's easy to find companies that provide "VPN services", generally in the if-you-want-to-know-what-it-costs-call-us-and-we'll-send-three-salesthings price bracket. Some of these services involve leased-line connections so your data doesn't pass over the public Internet. They're generally sold to paranoid executives, with the private line touted as a security feature. But, given the exceedingly solid nature of the open encryption protocols in common use today, leased-line VPNs are more about bandwidth and connection reliability, really.
Some of the VPN setup services, though, are basically just consultancy, which may be massively expensive for what you get. They're often hawking expensive software with per-seat license expenses; the SnapGear boxes have no such artificial limitations.
OK, it takes some know-how to get a major corporation's complex network connected over the Internet. But if you're not a major corporation, all you need are a couple of half-way competent IT staff and some SnapGear-ish boxes for a solid solution.
Even home users can get in on the act easily enough, and run VPN servers if they want, not just clients.
All you need to connect to a PPTP VPN server with a Windows machine is the IP address of the server, and an account name and password.
Making VPN accounts via the SnapGear interface is simple enough, as is setting the IP address from which VPN data will appear to come, from the LAN's point of view, and the IP addresses that'll be doled out to people who connect, from their point of view.
You can run a PPTP VPN server on the LITE+ even if you don't have a static IP address, but everyone who wants to connect to your server will need to know what your address is today. Many consumer broadband users, including me, have a de facto static IP address - their address is leased with a long lease period, and there's no guarantee that they'll get the same address again when the lease expires or when they release and renew for whatever reason. But, in practice, the address never changes.
Dial-up Internet users won't have a static IP address unless they've paid extra for one, but running a VPN server on a dial-up machine is pretty perverse anyway. A client can connect from any IP address they like.
Note that running any sort of server, including a VPN one, is a violation of many consumer broadband ISP's terms of service. Note also that most of them don't actually know or care if you're doing it, as long as you're not shifting awesome amounts of data. If you exceed whatever their hard or soft data transfer limits are, they bust you; if you don't, you can generally be running 408 different kinds of server and not get so much as a nastygram from your ISP.
Further oddities
While I was reviewing the LITE+, it behaved itself perfectly for a couple of days. Except for the easily-fixed "timing issue" glitch, which no longer exists with the current firmware, it worked pretty much exactly as advertised.
And then it didn't.
One morning - well, afternoon, to be honest - I got up and found that my LAN was no longer on the Internet, and hadn't been for some hours. I'd been fooling around with VPN stuff before I went to bed, but everything had been working fine then. And now it wasn't. The LITE+ was visible on the LAN, its setup pages worked fine, it thought it was connected, but no data made it through the router. It looked like the previous timing problem, back again to haunt me.
To make a long story short, Optus@Home's support said the cable modem hadn't been able to detect the router's MAC address, which was wrong. After some back-and-forth with SnapGear support it seems likely that at some point I'd set up the LITE+'s DHCP server to report the LITE+'s IP address as the Internet gateway address - which it won't do by default. And then I hadn't. And when computers were restarted or their DHCP settings leases expired, they queried the LITE+ again and were now told that the gateway was the first valid address on my subnet. Which it might have been, but wasn't. Result: No connection.
Setting the DHCP server back to report the router's own fixed IP address as the gateway fixed this problem. But nothing on the router now looked any different from the way it did before, unless you pored over the config files and noticed a 192.168.0.2 where once there was a 192.168.0.1.
SnapGear have acknowledged that they need a minor interface upgrade here. It should be obvious in the normal DHCP Server setup page when the router's been told to send non-default gateway or DNS or WINS address settings, and what they are, and when it hasn't.
I'm happy to say that despite the instructions' insistence that you have to enter your ISP's DNS address manually, the SnapGear server's default behaviour is to pass through any DNS address it's got for the WAN side. Which means it Just Works. But you do need to manually set the gateway.
Before we got this sorted out, this article ended by saying that I was back to the Windows sharer box, because it worked and the other options didn't.
Well, now the SnapGear's handling my Internet connection again, and the Celeron box has once more been released for other duties. There doesn't seem to be any likelihood that the LITE+ is going to blow up or go bananas - well, there's rather less chance of that than there is that the Win2000 machine will do the same thing, anyway.
The Linux box still sits, abandoned, in the corner, with a driver for one of its network cards that should work, but doesn't. That network card apparently isn't actually supported by any version of Linux, as it turns out; if I want a driver for it, I'll have to write my own. Where the FreeSco people got the idea that they had a working driver for it, I don't know.
If you've downloaded a baby-Unix router package that supports some old hardware you have kicking around, you'll probably be able to get it working just fine. Lots of people have. But I didn't.
And some plastic-box routers have problems considerably bigger than the LITE+'s; with the current firmware, all it's got is a bit of an interface oddity, and that's hardly unknown. Even very popular consumer routers occasionally have continuing firmware issues, where each new release fixes some problems with the more advanced features even as it creates new ones. You shouldn't expect this to happen, but you shouldn't be astounded if it does. For a product from a quite new company, the LITE+ is pretty spiffy.
It's also fair to say, though, that the current NT-series Microsoft operating systems really do handle the basic Internet sharing task perfectly well. Not elegant, not cheap, not particularly featureful, but good enough. Win98SE and WinME aren't stable enough for the job, but Win2000 and WinXP are.
Overall
SnapGear's LITE+ is not the world's cheapest router, and it's not got features that you can't find anywhere else, but it's a good feature set for the money and, with the current firmware, it's easy enough to set up for both plain Internet sharing and VPN purposes. If you want a gadget that you click two cables into and press a button and bang, your Internet connection is shared, then no such product exists anywhere. But it doesn't get much easier than this.
SnapGear's documentation could be better, but it doesn't stink. The Web interface is quite good on the whole, though there's room for improvement there as well. The things the SnapGear routers lack aren't necessarily things you want, and their VPN capabilities are excellent for the money.