Lifeview Finger ID
Review date: 3 March 2001.Last modified 03-Dec-2011.
Biometric identification isn't just coming, it's already here.
Biometrics is the study of measurable biological characteristics or, in computer parlance, the use of these characteristics to identify people. A good biometrics system lets you use your voice, or your iris pattern, or your fingerprint, to identify yourself. You don't need to remember a password, you don't need to carry a card or a key; as long as you haven't had a nasty accident on the weekend, you can log in to the super-secure database on Monday.
The neatest and most affordable biometrics gizmoes at the moment are fingerprint scanners, which generally have a little half-inch square sensor you put your finger on. They'll be pretty mainstream items soon enough, commonly built into mouses or keyboards, or low-cost stand-alone devices.
There are still plenty of people selling these things for more than $US200, but they're no longer obscure nutty-tech. Dell can do you a PC with fingerprint scanner logon for $US100 or so above the normal price. A whole company-wide properly administered rig can cost serious bucks, of course, but standalone workstation pricing is reasonable.
And here's another affordable finger scanner, from Lifeview.
The Finger ID is a $AU264 USB finger scanner that comes with security software, and while it's got some rough edges and some significant limitations, for what it is, it works well.
Setting up
As a USB device, the Finger ID's a plug-and-go proposition, with Windows drivers on the accompanying software CD. Plug in, point Windows to the driver, install support application, start scannin' fingers.
Amazingly, the manual's an OK guide to installing the software.
I say "amazingly", because of the introduction, which doesn't bode well for the comprehensibility of the rest of the booklet. The intro says, and I quote:
"Finger ID, Security for your e-commerce, and suitable for secure any process need password, using fingerprints is more reliable instead of Password. With the Life Layer of your skin whatever that is dry, thickly callused, or worn smooth. It's highly reliable e-commerce is the future's trend and now shopping on web already instead of go out shopping. Passwords only have few numbers, guess out is very easy. But there's no second fingerprint same with yours in the world. Secure your life, with the unable reproduced fingerprints. Let our life has the best quality. Secured our life by USB Finger ID."
The "Life Layer" stuff refers to the fact that the sensor in this thing works by transmitting a very small signal from the silvery "drive ring" around the sensor pad to a load of what are, in effect, very small antennas inside the sensor. The antennas detect, with exquisite accuracy, how far from them the conductive, live layer of skin is. That layer conforms to the shape of your fingerprint, so it doesn't matter what state the less conductive dead layer of skin on the outside is in. If your finger isn't so damaged that you're bleeding all over the Finger ID - and, possibly, even if you are - your print will be readable.
The rest of the manual is, thankfully, less wordy and more comprehensible, and it describes how to install the Finger ID device in Win98, Win2000 and even Windows NT.
Ah, I hear you say, but WinNT doesn't support USB!
True.
The FingerID installation disc includes an NT USB stack, which should allow the finger scanner to work. Like all NT USB stacks, this is a limited one, which won't work with most peripherals - possibly not anything but the FingerID, in fact.
This whole question is actually completely immaterial for most users, because this is really only a product for Win95 and Win98, as I'll explain in a moment.
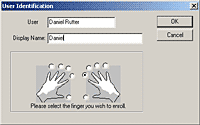
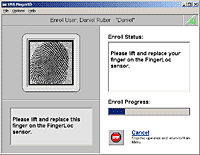
Here's the included recogniser software. To "enrol" a user, you name them and say which finger you're scanning. You can do all ten, if you like, which ought to take care of most problems of the I-got-drunk-and-played-with-a-bandsaw variety.
The enrolment process is fast; press on the scanner a few times when you're prompted, and you're done. The software checks the scan afterwards to see if it can recognise the finger, which it always seems to do. As long as you get your finger more or less properly on the scanner, it works.
It's not fussy, but neither does it ever seem to mistake one finger for another, as far as I can see.
This software, however, is just decorative. It works on Win98 and Win2000 and, probably WinNT as well, but it doesn't handle login or file protection or anything else. It just makes a database of fingers. You can use it to ID people, but it won't do anything except tell you who just put their finger on the scanner.
If you want something practical to happen, you have to install the other package from the software disc.
The real software
The proper software for the Lifeview scanner is BVI's pcE BioSecure, and it only runs on Win95 or Win98. WinME support isn't mentioned, so there probably isn't any.
The scanner uses AuthenTec technology (a FingerLoc sensor), so anything that supports an AuthenTec finger scanner should support the Lifeview one. If you've got WinNT or Win2000 (or Linux, or BeOS, or whatever) software that supports this kind of scanner, you can leave the supplied software disc in the box and go for it.
There's also developer information on the software CD, and some API/SDK stuff gets installed when you install the decorative scanner software. So if you want to develop a finger-scan application, this package could be a good start. If you don't already have finger-scan software for your OS of choice and you're not a programmer interested in this field, though, forget anything but Win95 and Win98 support, for the time being.
Normally, using any sort of serious access control software with the Win95-series OSes is like putting a ten kilo combination lock on a cardboard box. Win95 and Win98's password login system is a convenience feature, so multiple people can have different desktops and My Documents folders and so on. It's not a security feature. Anybody can trample anybody else's files, and anybody can get around the login completely if they want to.
BioSecure, however, does a surprisingly good job of keeping data secure. Well, unreadable, at least.
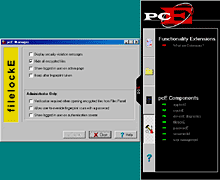
When you install BioSecure, it asks you to set up an administrator account and optional user accounts as well, if you like (the administrator can make more accounts later, of course), and then it replaces the standard Windows logon with a fingerprint system. Once you restart and log in with the finger scanner, there's a toolbar thingy that lets you configure the security software.
BVI have rolled their own interface, but it's simple enough and straightforward to use. The BioSecure software has lots of features, all of which work pretty well. Despite BVI's obsessionE withE puttingE aE trailingE capitalE EE onE everythingE.
"LoginE" is the fingerprint logon program. If you've got the wrong print for the username you entered, you can't log on. There's no simple Cancel box that lets you walk around the logon.
This being Win98, of course, you can still start up in Safe Mode. Presto, no logon of any sort and full access to every program on the computer. But this is not as much of a slam-dunk as it seems.
It beats one BioSecure feature, all right. The "applockE" feature lets you lock programs so they won't run if you're not the person who's meant to run them. As long as BioSecure's running.
If you've started in Safe Mode, the programs run again.
This is because of BVI's sensible decision not to monkey with the actual program files. BioSecure just wedges itself into the program execution process and causes Access Denied errors on anything that's meant to be locked, until it gets a fingerprint it likes.
The BioSecure task doesn't show up in the Ctrl-Alt-Delete Close Program dialog, but nobody with a passing familiarity with the fine products of radsoft.net, or any of the other utilities that lock Vise-Grips onto Windows' nipples and let you twist them to any angle you want, should have any trouble removing the application lock without even rebooting.
BioSecure does have less cosmetic features. The "filelockE" feature lets you encrypt files so they can't be read unless you're logged in as a person with read permission for that file - and read permissions can be assigned to one person or to a group.
By default, BioSecure uses the highly secure Blowfish encryption algorithm, but I don't know what key length it uses by default. More on the fascinating Maths Can Be Fun subject of keys and where they come from in a moment.
The "screenlockE" feature gives you a fingerprint-protected screen saver, allowing you to show off your biometric toy more often. I mean, effectively prevent unauthorised access to your computer during the working day.
Finally, the "passwordE" feature lets you assign password macros to be fingerprint-activated, so applications that require you to logon just require a fingerprint instead. The logon macros are, of course, also encrypted, so unauthorised people can't lift your user name and password for whatever you log onto.
Problems
BioSecure's not absolutely 100% baked just yet. It does quirky things from time to time. For instance, when I hit the cancel button on the finger-scan prompt for a locked application, BioSecure lost the ability to show the prompt again - and, therefore, couldn't run the application. For a while. Then it learned how to do it again. Beats me.
There are some more annoying glitches, too. One of 'em goes like this.
When BioSecure's running, and you've got the default hide-encrypted-files option selected, all of your encrypted files are invisible to anybody who, say, looks at your machine over the network. They'll be invisible to other users of the computer, too. No problem.
Start in Safe Mode, and the files are visible and you can see what they're called. Their contents are just encrypted nonsense, of course, but you can delete them if you like.
If someone changes the contents of one of your shared directories in any way, though - by creating a new file in one of them over the network or after starting your machine in Safe Mode, say - then when you're logged in to BioSecure normally, that directory will now seem to be empty except for the new file or files. All of your files vanish.
Except they don't, really. They're still visible in the BioSecure file-view control panel thing, which is just a big ugly alphabetic list of files with no directory structure. You can open and rename and delete them as normal from there. But you can't make them reappear in the folders by any means, as far as I can see. There's a utility to repair locked applications that have gone wrong, but it does nothing for vanished files.
This is just an inconvenience, but it could be a scary one the first time you saw it.
Getting technical
OK, so what's this thing doing with your fingerprint, exactly?
A prime concern with all security systems is how resistant they are to all sorts of attack. It's bad form to over-sell a security system, but various companies, including BVI, do it.
Anybody who has physical access to your computer can destroy all of the data on it. Formatting the drive. Deleting files and then defragging to make undeletion impossible. Loading encrypted files in a text editor, adding random rubbish and saving them again. Just taking the hard drive out of the computer and smashing it.
No encryption system or operating system can save you from all of these attacks on data to which an attacker has physical access. BVI tell you to go to the BIOS setup and disable boot-from-floppy, and lock the BIOS setup program with a password. They don't mention that if you've got access to the computer, you can always clear the CMOS (yank power cord, set appropriate motherboard jumper for a few seconds), and you don't even need to, if you just booting into Safe Mode.
All that said, though, there's still the encryption side of things. Destruction of data's no big deal, if you've got backups. Attackers being able to read encrypted stuff is, probably, worse. If it isn't, there's no reason to encrypt it. I'm happy to say that on the encryption count, BioSecure seems pretty good.
Here's how I know.
First, think about how normal passwords work.
Having, say, 128 bit encryption on something means little if the password that gets converted into a key that decrypts the data only contains, say, 20 bits of information. Anybody who has the right key can decrypt the data, and anybody who can guess the password can get the right key.
There are exactly 1,048,576 possible 20 bit numbers. No more, no less. A password cracker can feed all of them to a key generator, and see which of the keys can be used to decrypt the data, very quickly indeed.
You can use an algorithm that generates a 128 bit key from a 20 bit source, but within the far, far larger number of possible 128 bit numbers (there are about 340 million million million million million million of them...) there are many, many other sources that will generate exactly the same key as any given 20 bit number.
If your key-source has 128 bits, then it is the one and only source that will generate a given 128 bit key. Cracking it will, unless a brute-force attacker is stupendously lucky and stumbles on the right number early, take long enough that the sun ought to have long since swelled to swallow the earth by the time the code's been broken.
With only a 20 bit key-source, though, you make your ironclad 128 bit encryption approximately 324,518,553,658,426,726,783,156,020,576,260 times easier to crack. Any half-competent programmer could probably do it in an afternoon. Including the time taken to write the cracker software.
If an attacker's just trying "brute force" password cracking, short key generation strings - passwords - make it easy. The attacker doesn't have to guess your password, just one of the many other possible ones that create the same key.
You can get almost six bits of data per character - the equivalent of 5.954 truly random bits - if you choose a random password composed of upper and lower case letters and numerals only, to make it typeable. So something like "dU5n2yDu9RHsj2A" is good for about 89 bits.
Many people do this in a half-hearted way, semi-randomising English words by vaguely l33t number substitution and giving people passwords like "b33fh3art". Which is great, unless your attacker has a dictionary-attack program that automatically tries the numeral one in place of "L" and "I", the numeral zero in place of "O", and so on. If he does, l33t passwords fail almost as rapidly as plain-English words.
This happens, though, because no bugger can remember a proper random password of any significant length. Certainly not the 22 characters you need to get over the 128 bit mark. OK, Raymond Babbitt would probably find the task trivial, but most of us wouldn't.
To avoid users committing the cardinal sin of writing down their passwords on Post-It notes stuck to the monitor and making the whole idea pointless, you therefore need to use plain, memorable English for your passwords, if you want lots of bits. You can l33tify it if you like, but it's simpler to just use more words in your "passphrase".
English words have an information density of only about 1.2 bits per character (because they're a darn long way away from randomness), so you need about 107 characters, which is around 21 words, for a solid 128 bit passphrase. It shouldn't be a famous quotation, as those are vulnerable to dictionary based attacks, but it can be a perversion of one. "Now is the Britney of our discontent made glorious bummer by a fishy spork" has about the same real random-number-equivalent bit length as the "dU5n2yDu9RHsj2A" password above, but it's much more memorable.
It's still a pain to type, though.
OK, so let's move on to the fingerprint system. Here, the "password" being used to generate the encryption key is the fingerprint image. Which gives you an easy way to enter a lot of distinctive data, like a passphrase, but with just one squish of a finger.
Naively, the 128 by 128 sensor resolution of the FingerLoc device would appear to give the Finger ID 16,384 bits of output data, from which could be sampled a key of anything up to that length.
Given that all you really need for a key nobody's going to be able to break easily is 64 bits, this would appear to be fine.
But every time you put your finger on the sensor, you create a quite different result. The pattern's the same, sure, but it's shifted around, and you get different amounts of it on every attempt.
What fingerprint recognition systems therefore do is convert the pattern to a "template" - a description of the characteristics of the fingerprint, akin to a vector graphic image file, as compared with a bitmapped one.
So you're not generating the encryption key from something that says "black pixel, white pixel, white pixel, black pixel", et cetera; instead, you're generating it from something that says "loopy thing next to swirl with a leftwards bend in it, nine concentric oval ridges in the middle before the tenth one opens out into a U..." and so on.
Actually, pretty much all digital fingerprint recognition systems do their thing by looking at "minutiae" - points where ridges on the print start, stop and join. There are 30 to 40 of them per print, and their locations relative to the "core" of the print are sufficient to identify someone. It's not likely that two people will share more than eight minutiae. There can be information on ridge counts and actual layout as well, but there doesn't need to be, with a decent crop of minutiae.
The excellent accuracy of the Lifeview recogniser indicates that a relatively large amount of variation in the pattern must be acceptable. If it was picky about the exact layout, it would reject valid prints more often. The question is - how many real good-as-random bits is this thing extracting from the template?
The answer is - quite enough, thank you.
Apparently, templates work out at about a kilobyte in size depending on the technology used to make them, but if you've got, say, an exactly 1024 byte template, that doesn't mean there's enough real data in it to make a true 8192 bit key. You'd have to compare lots of templates to see how different from each other they really are; only if they're completely unrelated, and all look like random hash, does their size truly indicate their cryptographic usefulness.
If you assume that, to manage good matching of imperfect finger-scans, you've got 40 minutiae plotted as unqualified dots on a 32 by 32 grid, then you need ten bits to express the location of each dot (since there are 1024 places it can be - 32 by 32), and you've got a massive 40960 bits of real data.
If the template's resolution is only, say, 20 minutiae on a mere 8 by 8 grid, then you've still got 120 bits. So it looks as if you're in business.
How much the Finger ID system has to do with the possibilities implied in the ANSI/NIST Data Format for the Interchange of Fingerprint Information I don't know, but if it even comes close, 128 bits shouldn't be a problem at all.
Hole-hunting
The BioSecure administrator has an optional override password, in case the biometric device fails; all of the users can have one, too. The admin override password, however, only allows access to everything except private encrypted files, and the user passwords only let them do what they could if they'd logged in with a fingerprint.
Unfortunately, there's nothing forcing the override passwords to be strong. I successfully made my override password "a". A brute force attack on these lousy passwords could be successful in an embarrassingly brief period. Like, a small fraction of a second.
OK, you'd have to crack all of them, but J. Random HaXXor could do it.
This, at least, reduces the need for a determined attacker to cut fingers off people. If an attacker's ruthless enough to cut a finger off a user, he's probably also ruthless enough to do what it takes to get passwords out of the same user by, for instance, threatening to cut their fingers off.
The Finger ID reader is supposed to reject, um, no-longer-alive fingers, anyway. Though I'm not sure how it does it.
Differences in conductivity, I suppose; if you pickle a severed finger it probably won't work, but if it's freshly cut it probably will. It's not just a temperature thing; I frosted my fingertip with freezer spray in the interest of scientific inquiry and still logged in fine.
Further investigation in this area is on hold, pending the capture of some suitable experimental subjects.
There may be some huge gaping hole in the pcE system that I haven't noticed - I'm no crypto-guru. The administrator's ability to export user profiles seems to be a hole, since Blowfish is a symmetric crypto system (it uses the same key for encryption and decryption) and he who holds the key would appear to be able to decrypt whatever he wants. But I'm probably missing something.
Overall
The hardware and print-recognition side of the Finger ID system is excellent. The software side, not so much.
BVI's spiel for BioSecure is that "you and only you can access your computer and keep your sensitive information secure", and that's sort of technically true, but the system doesn't stop other people from accessing your computer and taking a great big poo on your sensitive information, without having much idea of what it is. If BioSecure ran under Win2000 or WinNT there'd be more protection, but if someone nasty's got physical access to your computer, you're still essentially boned.
BioSecure doesn't stop your hard drive from crashing, or your computer from being stolen, either. All it does is stop anybody from being able to read your encrypted files or log in normally to your computer.
You can deal with the various things that can destroy your files by backing the files up, as normal. If you back up encrypted files when you're not logged in as somebody who should be able to read them, they're backed up in their encrypted form. If you back them up when you are able to read them, they're backed up in their plaintext form. This isn't a problem, as long as you know about it.
If you want a reasonably secure fingerprint login system for a Win98 or USB-capable Win95 system, this one'll do you. If you just want a standard USB AuthenTec fingerprint scanner to use with some other software, here one is.
Until the software gets a bit more elegant and the consumer operating systems get a bit more secure, though, this isn't a product most people want or need. For most users, including many business users, a thing like this is still just a cool toy.